My wife and I recently had the opportunity to give our kids a one-day whirlwind tour of the US capital. Driving south to meet up with family, we stopped in DC for the evening, (planning to jampack our Saturday), with reservations at the fine Omni Shoreham hotel.
The weirdness started with parking. Located by Adams Morgan, it’s valet-only, but signs indicated the lot was closed, with cars backed-up and stacked-in. We found a spot to idle while my wife ran inside to check, and I sought out a harried, overwhelmed-looking valet.
He wrote down my information on a scrap of paper and promised to come soon. But no one did.
Inside the massive lobby we found lines backed up around the corner, and talked with other guests who were baffled at delays and snarled services, which had apparently been going on the day before, too.
The lights were on, the TVs going in the bar, and eventually someone came for our car. But in the lobby, the lines barely moved, and tensions from a broad range of guests were boiling over.
Staff circulated with bottles of water, apologies, and tired smiles. One man told us he’d worked through the night, raced home to grab a shower and four hours sleep, and came right back.
Like most everyone we met at the hotel, he was working hard to see them through a crisis, with guests increasingly frustrated (or downright outraged). Services only seemed to work via phone calls and runners, bars and restaurants running manually, and cash-only.
They were having an IT outage, we were told at 1 AM when we finally checked in (my exhausted kids slumped on the lobby couches with other peoples kids). Their systems were down everywhere. And while no information was available then, this was all fallout from a ransomware attack.
For my family, it amounted to a memorable inconvenience—the beds and showers still worked, they eventually found our car at check out, and we still got our Washington DC visit in.
But for the staff at Omni hotels across the country, it was a nightmare.
In this week’s The PTP Report, we look at ransomware up close: revisiting the Change Healthcare attack and considering ways that organizations can protect themselves from this disturbingly frequent, and increasingly insidious, form of cybercrime.
[For our original coverage of the ransomware attack that’s plagued UnitedHealth, check out the cybersecurity roundup from January–March.]
Ransomware: Real World Impacts
Ransomware is a household term, but it refers to a highly specific kind of cybercrime—when an assailant locks up a target’s systems and demands payment to restore them.
It’s typically done via data encryption, with the means to decrypt only being given on ransom payment.
Those impacted have the choice of paying the ransom, or shutting everything down, finding and resolving their point of entry, and then restoring from backups (if they have them).
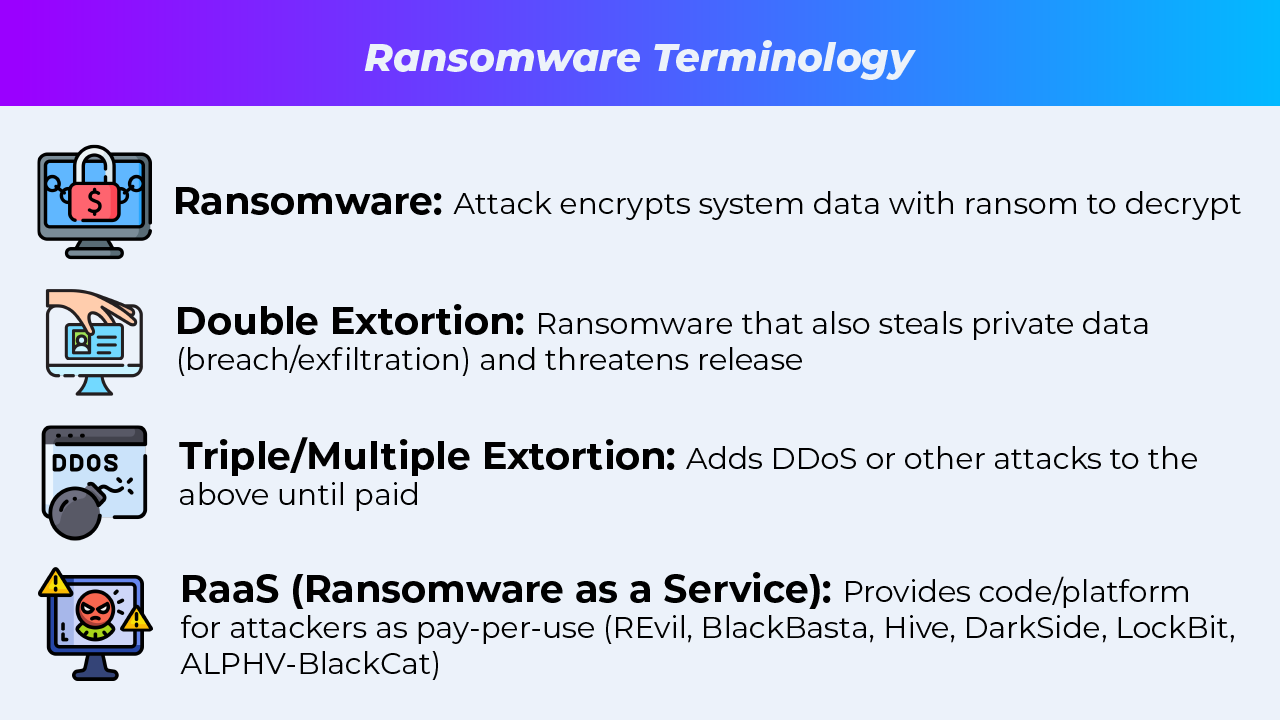
Increasingly, we see attackers also layering on a data breach, in what’s commonly called double extortion, with the threat to leak stolen personal data to accelerate, or increase, their ransom demands.
This is the kind of attack that hit Omni Hotels and Resorts, who shut down systems across their resorts on March 29—impacting reservations, point of sales, and even room key entry—only getting them back up on April 8.
The Daixin Team took responsibility for this attack, demanding $3.5 million in ransom, and claiming they’d also stolen the personal data of 3.5 million guests.
In a public statement, Omni warned on April 14th that customer data may have been stolen from the hotel, but only amounting contact information (not financial data or social security info).
Sophos, in their State of Ransomware 2023, found that 30% of ransomware events last year added this data exfiltration aspect, with additional forms of attack—such as a Distributed Denial of Service (DDoS)—sometimes being piled on as another vector to force payment. That kind of attack is akin to flooding a target with so much traffic, or unwanted access, that they are overwhelmed.
Many of the attackers don’t even use their own code—instead leveraging RaaS (Ransomware as a Service) entities who provide malware on a pay-per-use basis, sometimes even managing the transactions.
While international law enforcement has made a concerted effort to break up some of the biggest RaaS providers, Zscaler estimated in 2022 that 8 of every 11 ransomware attacks came through an RaaS.
Change Healthcare
As taxing as the Omni Hotel ransomware attack was for its staff, guests, and the company itself, it pales in comparison to damage wrought at Change Healthcare.
The most devastating cyberattack ever in healthcare (and arguably of any kind), became public this February. Change, which is owned by UnitedHealth and provides revenue and payment management across providers and patients, was shut down by an RaaS attack from ALPHV/Blackcat that paralyzed medical services across the nation.
Many patients suddenly found themselves with appointments rescheduled, procedures being inexplicably delayed, and payments for services failing.
Many prescription drug copayments were suddenly denied, forcing people to pay out of pocket, if they could. In extreme cases, cancer patients needing specialty drugs as costly as $20,000 were unable to afford them, leaving some providers to do everything they could to try and get desperate patients what they needed to survive.
Four out of five physicians in the United States lost revenue because of this attack, Forbes health care contributor Bruce Jaspen told NPR, with damages running as high as $100 million per day, and driving practices, in some cases, out of business.
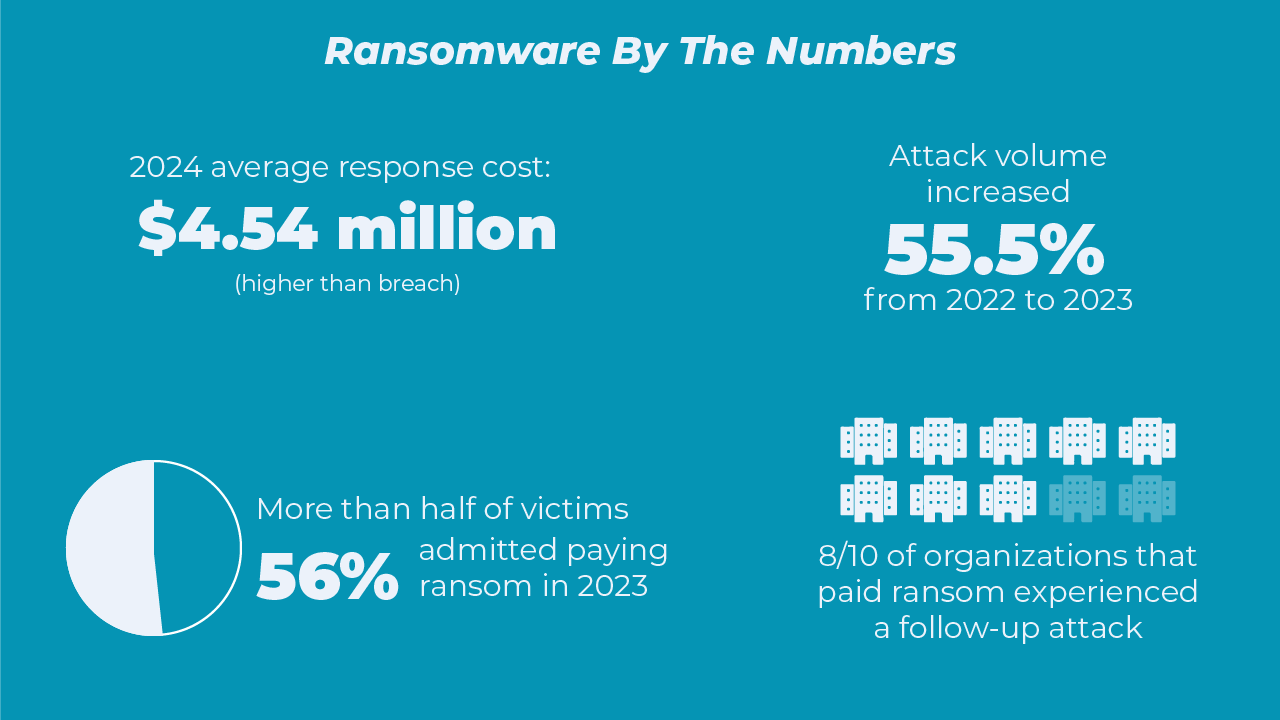
The fallout cost to UnitedHealth is over $1 billion and rising, and some of this expense will most certainly be eventually passed to customers, with premiums expected to rise to cover the extreme losses.
Making matters worse, the attack included additional extortions, likely to impact what Jaspen called “a substantial proportion of people in America.” Data leaked from Change includes names, emails, addresses, and potentially social security numbers and credit card information.
But so far, despite threats from the perpetrators to the contrary, evidence hasn’t been found of the worst-case scenario: leaked medical records.
On Ransoms
While most ransom payments do result in organizations getting their data back—Sophos estimates 97% of organizations did so in 2023, either from ransom payment or backups—paying them also triggers additional attacks. 8/10 of those who paid ransoms were hit again by ransomware attacks; sometimes within months.
UnitedHealth later admitted to paying a staggering $22 million in ransom. CEO Andrew Witty wrote in a statement to the US House Energy and Commerce Committee that: “As chief executive officer, the decision to pay a ransom was mine. This was one of the hardest decisions I’ve ever had to make. And I wouldn’t wish it on anyone.”
And unfortunately, their problems didn’t end there. The hefty ransom payout only dealt with the initial extortion, with additional demands coming after, and the ransom group involved appearing to break apart in a chaotic mess that includes faked takedowns, conflicting demands, and remains without clear resolution.
Defense and Mitigation
If organizations can take lessons from these ransomware horror stories, it’s to do whatever they can to protect against them before it’s too late.
The Change Healthcare ransomware attack was particularly frustrating, with CEO Witty acknowledging that:
“The portal did not have multi-factor authentication. Once the threat actor gained access, they moved laterally within the systems in more sophisticated ways and exfiltrated data. Ransomware was deployed nine days later.”
Breaking in was as simple as acquiring credentials, showing that phishing can be one avenue to open the door for these attacks.
The US Cybersecurity & Infrastructure Security Agency (CISA) provides cyber defense guidelines for organizations to protect themselves, and advice on how to handle attacks when they happen.
I list some cybersecurity best practices here, but for more, check out their full guidelines on protecting against ransomware attacks:
- Maintain offline, encrypted backups of all critical data
- Create, maintain, and exercise incident response plans, with communication and notification procedures
- Do not expose services on the web wherever possible
- Conduct regular vulnerability scans
- Always patch and update software and operating systems ASAP
- Implement phishing-resistant MFA for all services (email, VPN, accounts)
- Use smart password policies (15 chars+) with lockout after failed attempts, storing passwords in secured databases with strong hashing algorithms, and disabling saving passwords to browsers
- Educate all employees on password security, phishing, cybersecurity awareness, and how to flag emails
- Keep and secure logs and monitor them regularly as part of regular security assessments
- Establish a security baseline of network traffic and tune appliances to detect anomalous behavior
- Always allow the fewest people the least amount of access they need to do their jobs
- Implement a zero-trust architecture
[For more on zero-trust architectures, check out our The PTP Report on 2024 security trends.]
As always, organizations like PTP are here to help, providing cybersecurity experts, and expertise, to help your organization with protection as well as ransomware recovery strategies.
Conclusion
Ransomware is increasingly common, and easy to ignore. That is, until you can’t.
In our case, it was lines around the corner, cash-only services, and high tempers everywhere. Employees putting in extreme workloads, trying to smile at outrage, working to overcome a crime that happened upstream, on servers—in some cases—located half-way across the country.
At the Omni, the ransomware attack consequences weren’t life and death, but for some, they are. People impacted by the Change Healthcare attack found medical procedures suddenly off and desperately needed drugs inaccessible.
Practices, all over the country, were unable to complete transactions needed to pay their own bills, in a staggering domino effect.
It’s a wake-up call, not only for strong cybersecurity measures for hotels and healthcare, but for all organizations, in all sectors worldwide.
We must all be proactive in defense, prepared for the worst, and get strategies in place for resolution if we want to put a check on this insidious crime.
References
What we know about the hacking attack that targeted the U.S. healthcare system, NPR
Cybersecurity expert shares what guests, hotels should know in wake of Omni breach, ABC News
Omni Hotels & Resorts Update On Recent Cyber Attack, Omni Hotels & Resorts
Change Healthcare Finally Admits It Paid Ransomware Hackers $22 Million—and Still Faces a Patient Data Leak, Wired
Change Healthcare’s New Ransomware Nightmare Goes From Bad to Worse, Wired
2022 ThreatLabz State of Ransomware Report, Zscaler
Omni Hotels Data Breach: Why Are Hackers Targeting Hotel Chains? Techopedia
Change Healthcare hacked using stolen Citrix account with no MFA, BleepingComputer
#StopRansomware Guide, CISA





