Workday was breached by hackers in early August.
We dig into the details below, but the short form is this: intruders accessed their “third-party CRM platform” and stole “primarily commonly available” business contact information before the connection was cut off (quotes are from their press release).
Workday has acknowledged this is part of a larger campaign that’s targeting numerous companies in similar ways—accessing their CRMs (Salesforce in other disclosed cases, see below) using social engineering tactics—with the aim of stealing business information.
In today’s PTP Report, we detail what we know about this Workday breach, the broader social engineering campaign and who’s been targeted so far, the believed perpetrators behind it, current risks to companies, and how you can best protect yourself from a similar attack.
With Workday’s scale—75 million users under contract, providing services for more than 11,000 organizations including 65% of the Fortune 500—this news will hit home for many of our readers.
The Workday Data Breach Details
Workday is one of the world’s largest providers of HR and financial management services via the cloud.
Based in Pleasanton, CA, it is an “AI platform for managing people, money, and agents,” with some 20,000 employees. Given its reach and popularity, it’s long been a target for cyberattacks.
The breach in question occurred in early August and was disclosed on their blog on August 15. Their release indicates that hackers accessed information, though the company specified there was “no indication of access to customer tenants or the data within them.”
The stolen data is believed to be mostly publicly available business contact information like names, email, and phone numbers, likely taken to be used in future social engineering attacks.
Workday spokesperson Connor Spielmaker wouldn’t comment further to TechCrunch, nor answer questions about how many people were impacted and whether they were internal to Workday or customers, and if the company will be able to determine exactly what was taken. And while they say it’s “primarily commonly available” contact information, they don’t fully rule out customer information.
The company also links this directly to other social engineering attacks where employees are contacted by hackers in the guise of HR or IT personnel.
This is all that’s been disclosed at this time by Workday, but it lines up directly with a large number of social engineering–led breaches in recent weeks that have hit large companies in the form of Salesforce data breaches.
What’s particularly challenging about these attacks is that no digital vulnerability is being exploited, and in the other attacks of this campaign, no malware had to be downloaded onto the target’s machine. Instead, the target extends authorization to an attacker’s app that appears in the guise of trusted software.

These attacks have largely worked by fooling employees into approving a connection that leads to the data flow from the CRMs themselves.
Ironically, the data stolen in each attack may also make subsequent attacks more effective.
As Redflags CEO Tim Ward told IT Security Guru:
“Workday’s warning is correct; any information that attackers can use to increase ‘familiarity’ in subsequent social engineering attacks will significantly increase their impact.
Psychological effects like authority bias, cognitive ease, social proof, and the mere exposure effect mean we are more likely to trust communications from them…”
The Broader Campaign of Salesforce CRM Attacks
As mentioned, Workday is just the latest in a number of large companies that have suffered data breaches in a similar fashion.
In addition to those listed above, victims include Tiffany & Co., Chanel, Victoria’s Secret, Pandora, and insurance provider Allianz, and the attacks usually follow a similar pattern.
A Google Threat Intelligence Group post shares the details of their attack analysis after a June breach of one of their own corporate Salesforce instances.
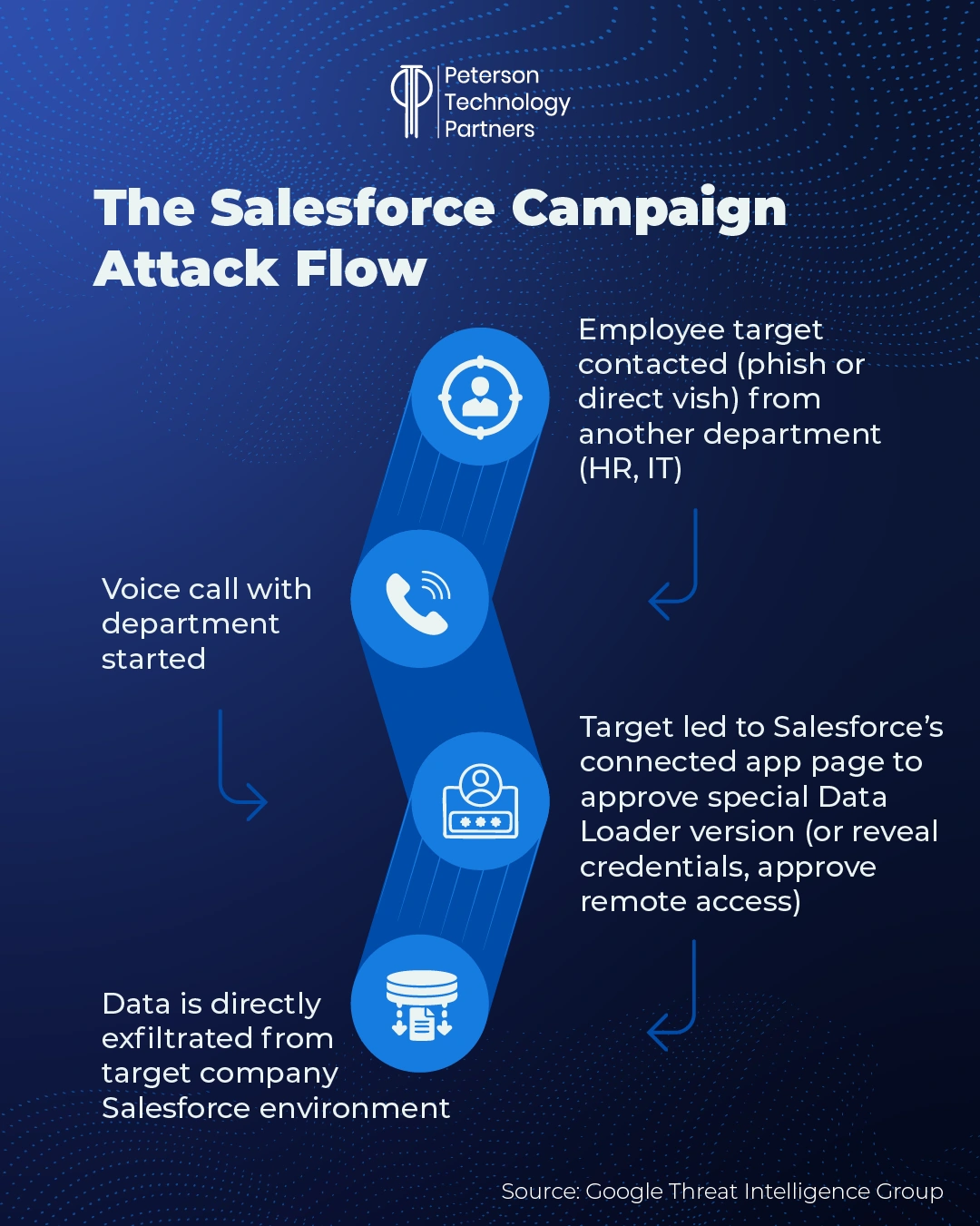
The attacks begin with employees at the target company being contacted (initially by phone or email) with the need to have a phone conversation with a member of the company’s HR or IT support.
These calls are described as being highly convincing, effectively disarming the suspicions of employees, often in English-speaking branches of global companies.
The employees are then led to authorize an application connection to their Salesforce instance—often a modified (but convincing) version of Salesforce’s Data Loader. This supports OAuth—in many cases attackers convince employees to open a Salesforce connect setup page and enter a code that links their Data Loader to this environment.
(Attacks have included both modified versions of Data Loader itself and also custom Python scripts that perform a similar function.)
This gives the attackers access to the Salesforce customer environment, and the hackers immediately begin to exfiltrate data.
In Google’s own case, the breached Salesforce instance was used for contact information and notes for small and medium businesses, and the attackers had only a small window of time to exfiltrate data before the connection was cut off.
A similar type of information appears to have been taken in the Workday attack.
Salesforce itself has not been breached, and their product does not have a vulnerability being exploited here, as the company pointed out to Bleeping Computer:
“While Salesforce builds enterprise-grade security into everything we do, customers also play a critical role in keeping their data safe—especially amid a rise in sophisticated phishing and social engineering attacks.”
It is the customers themselves who are opening the CRM to outsiders, and Salesforce has also documented this threat and provides recommendations via their own blog (see below).
The Group Leading These Social Engineering Attacks
In some cases, extortion activity has followed the breach (several months later), with these attackers claiming affiliation with the ShinyHunter hacking group.
The threat, if ransoms aren’t paid, is that a mass sale or leak will follow, as was the pattern with their Snowflake data attacks.
This well-known group emerged in 2020 and is linked to numerous large attacks, though these specific social engineering techniques—using highly effective phone calls for voice phishing (or vishing)—is a departure from their prior tactics and fits more with the Scattered Spider group, which we profiled in our June–July cybersecurity news roundup.
The two groups have been linked in a common community called The Com and may have overlap or even be synonymous. August reporting from The Hacker News details a Telegram channel that conflated the groups and suggested they were developing their own ransomware-as-a-service to rival LockBit.
This larger campaign is believed to have begun at the start of 2025 and to be financially motivated.
The Salesforce Data Breach Risks for Businesses
While there have already been some attempts to extort ransoms for the stolen data, in other cases it may well be that these breaches are being used to inform additional attacks.
As Black Duck’s Infrastructure Security Practice Director Thomas Richards told CSO:
“Every piece of information they gain in these attacks can be used to conduct further campaigns and get closer to their goals.”
Data Loss Prevention and Cybersecurity Best Practices for Protection
Attacks like these demonstrate that a vendor’s perimeter may be irrelevant to protecting your data.
It’s up to the companies themselves to continuously monitor and have sufficiently rapid detection capabilities in their own systems.
And with these attacks, defense begins with effective cybersecurity training.
Employees must be empowered to never give out sensitive information over the phone and understand they will be under no penalties for failing to comply with such calls, no matter the pressure of the situation or who is (supposedly) calling.
Companies can even provide short scripts for such refusals ahead of time, to further assist in responding and remove the pressure to comply with (the illusion of) authority.
If such practices are required, additional forms of verification must be provided to protect against scams like this and the rising effectiveness of AI deepfake technology.
In addition, Google Mandiant recommends enforcing IP-based access restrictions. By setting ranges and specific, trusted IPs and blocking commercial VPNs, companies can restrict access to their own networks. They should ensure logins and app authorizations from unexpected IP addresses are challenged or blocked.
Universal Multi-Factor Authentication (MFA) is essential for data breach prevention and overall security today, even if some of these attacks convinced users to bypass them (such as by providing the necessary prompt).
Within your training, prepare employees for specific means attackers can use to get them to bypass MFA.
Speed of response is also essential, and both Google and Workday claimed they were able to reduce the amount of data stolen by rapidly recognizing the transfer and terminating the connection.
Ensuring Salesforce Data Security
Limiting permissions to data access tools is essential. Within Salesforce, this can mean being very restrictive with the API Enabled permission.
Salesforce recommends reviewing your Data Loader access and configuring it to limit the number of users who can perform mass imports, updates, or deletions.
This should accompany regular audits and updates to ensure permissions remain set for least privilege.
Salesforce recommends avoiding blanket permissions at the profile level. Customizing permissions across connected apps and modifying Session Settings can help ensure unauthorized access can’t occur when users are away from their devices and Salesforce settings can restrict who can use connected apps and from where.
Salesforce multi-factor authentication (MFA) is used by the company itself and required to access their services by default.
Assistance from PTP and Salesforce Consulting Companies
The Salesforce Shield suite also offers tools for enhanced visibility and automated response. Its Event Monitoring gives extended information on data access and any changes, including when, by whom, and from where.
This includes more control for classifying your sensitive data and managing encryption, monitoring (or blocking) large downloads, and detecting threats like anomalies in usage or API calls.
As a Salesforce consulting company, PTP can help you ensure your own defenses are ready, providing Salesforce integration consultants to assist with implementations, app integrations, training, and ongoing support.
We also have nearly thirty years of experience providing top tech talent, so consider us if you need cybersecurity expertise to help establish a sound foundation or improve your training, monitoring, and response.
Conclusion: Ensuring CRM Security Now Includes Anti-Vishing Training
It may be a good sign of improving security that attackers are now resorting to such elaborate means to get data out of CRM instances, arranging complicated fake calls and posing as coworkers from other departments or branches.
On the flip side, these kinds of calls are hard to block and prevent, and the social engineering involved is being described as extremely effective.
While neither Workday nor Google suffered a technological vulnerability that opened their data to hackers, they were breached nonetheless—and these attacks continue to be successful even as so many occur and are reported on.
For help preparing your own people, you can also take a look at Mandiant’s guide to vishing for a detailed dissection on voice-based social engineering attacks.
References
Protecting You From Social Engineering Campaigns: An Update From Workday, Workday blog
Workday Data Breach Bears Signs of Widespread Salesforce Hack, Security Week
ShinyHunters and Scattered Spider: A Merger of Chaos in the 2025 Salesforce Attacks, Obsidian Threat Research Team
HR giant Workday says hackers stole personal data in recent breach, TechCrunch
Workday Discloses Data Breach Following CRM-Targeted Social Engineering Attack, IT Security Guru
Chanel data breach exposes US customer information in latest Salesforce attack, Cybernews
Pandora confirms data breach amid ongoing Salesforce data theft attacks, and HR giant Workday discloses data breach after Salesforce attack, Bleeping Computer
The Cost of a Call: From Voice Phishing to Data Extortion, Google Threat Intelligence Group
Protect Your Salesforce Environment from Social Engineering Threats, Salesforce’s The 360 Blog
Cybercrime Groups ShinyHunters, Scattered Spider Join Forces in Extortion Attacks on Businesses, The Hacker News
ShinyHunters strike again: Workday breach tied to Salesforce-targeted social engineering wave, CSO
FAQs
Was Workday’s cloud breached in this attack?
No. The breach that occurred leaked data from a third-party CRM that is used by Workday. The company divulged on its blog that this is believed to be primarily commonly available business contact information, but it’s not clear what else may have been included or if/when they may know for certain.
In attacks like this, how are defenses like MFA bypassed?
Attacks in this campaign begin with social engineering, wherein the hackers effectively contact employees at large organizations using the phone, convincing the target they’re from other departments like IT or HR. These conversations have been described as highly effective.
The targeted employees then enter their CRM connections page and use a provided code to authorize a connection to the hacker’s software. This software then extracts data from the CRM, and it’s up to the company to detect this transfer and stop it ASAP.
How do I guard against the Salesforce or Workday vulnerability that is being exploited?
No vulnerability in Workday or Salesforce’s software is being exploited. Instead, the attackers are fooling employees into opening the door and connecting their instance to the attacker’s own software. Sometimes this takes the form of a convincing fake—or altered—Salesforce Data Loader.
But again, these breaches are initiated by vishing, not through software vulnerabilities.





