It’s the end of May, 2024, and across America, doctors and nurses are using handwritten notes to chart patient issues. They’re sending faxes, and delivering orders by hand for tests and prescriptions.
In 19 states, facilities associated with Ascension, one of the largest private healthcare systems in the US, have patients stuck in emergency rooms, waiting for lab results and reading machine results without the assistance of electronic uploads. They’ve diverted ambulances, as thousands of medical professionals revert to old methods because of a ransomware attack.
It’s an attack eerily reminiscent of the Change Healthcare event that paralyzed a healthcare billing system that handles a third of all American patient records, and is detailed here.
It’s also an experience becoming all too-common in American healthcare, and we’ll look at the group behind this, and other cybersecurity highlights from the last two months, in our bi-monthly, Q2 cybersecurity roundup 2024.
[Check out our prior cybersecurity roundup, for Q1 cybersecurity trends.]
With so much going on, it’s our goal to help keep you informed, so you can be as proactive as possible with your data security, and overall cyber defense!
Headline Events for April and May
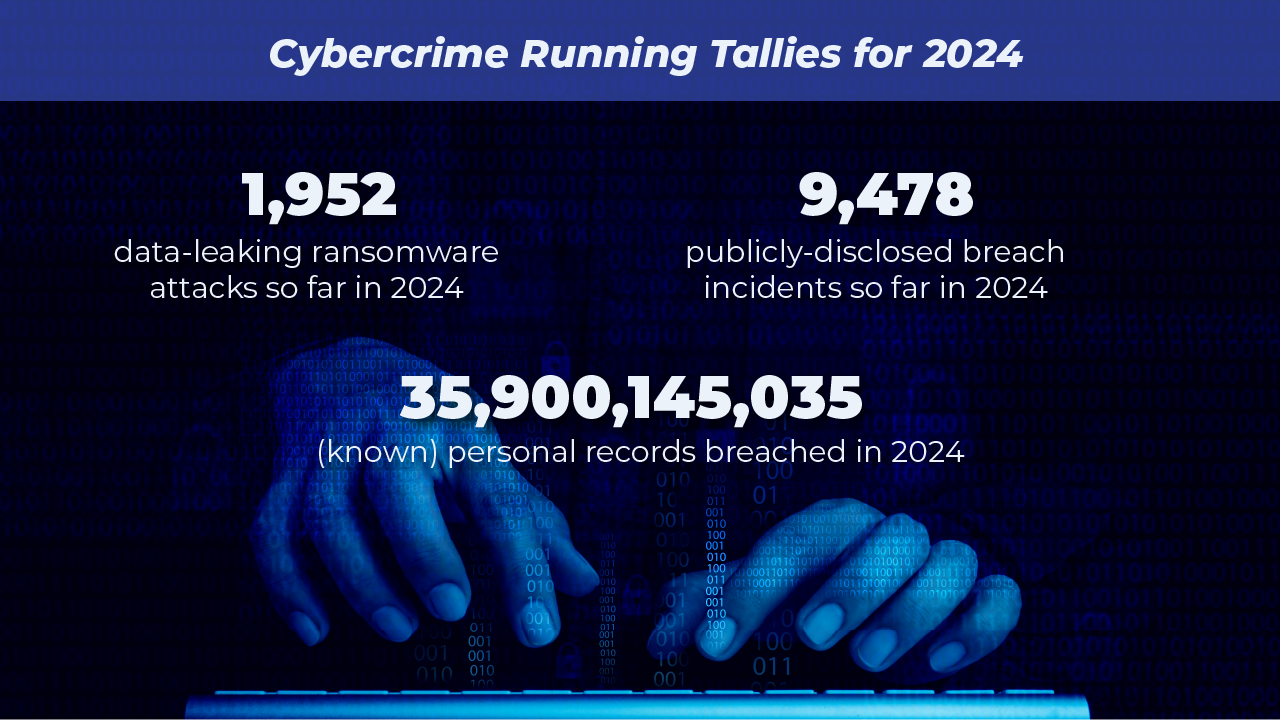
We start with the biggest cybersecurity news, across the varying forms of cyberattack:
- XZ Utils Backdoor: In April, a single person (a PostgreSQL developer at Microsoft), discovered a startling aberration in the popular Linux compression utility: a backdoor someone had spent two years painstakingly installing. Known as a supply chain attack, it involves hiding malicious code in an otherwise legitimate system. This specific backdoor would have ended up on many millions of systems worldwide, making it one of the most dangerous vulnerabilities ever perpetrated, had it not been sniffed out when it was.
- Black Basta’s Rampage: In May, a joint advisory posted by US agencies warned that ransomware-as-a-service (RaaS) operation Black Basta had targeted more than 500 organizations. “Black Basta affiliates use common initial access techniques — such as phishing and exploiting known vulnerabilities — and then employ a double-extortion model, both encrypting systems and exfiltrating data,” the bulletin warned. It’s believed that the Russian-speaking Black Basta is behind the Ascension attack and has successfully hit at least 12 of 16 critical infrastructure sectors.
Security firm Rapid7 revealed a unique form of social engineering used by Black Basta, wherein they flood a target’s inbox with spam emails, and then follow up with a fake IT call. They claim they can resolve the issue if given remote access to a user’s machine temporarily, which they then use to seed their ransomware.
- LockBit’s Big Boss Revealed: Sticking with RaaS, the US, UK, and Australia charged a Russian national they believe to be the leader of the LockBit ransomware group. With more than $500 million in extorted ransom payments, across more than 2500 victims, in at least 120 countries, it was a significant victory for authorities, who had seized darknet LockBit websites earlier in 2024 but failed to identify the supposed mastermind. The US Justice Department is urging victims to continue to file official complaints.
The Breaches
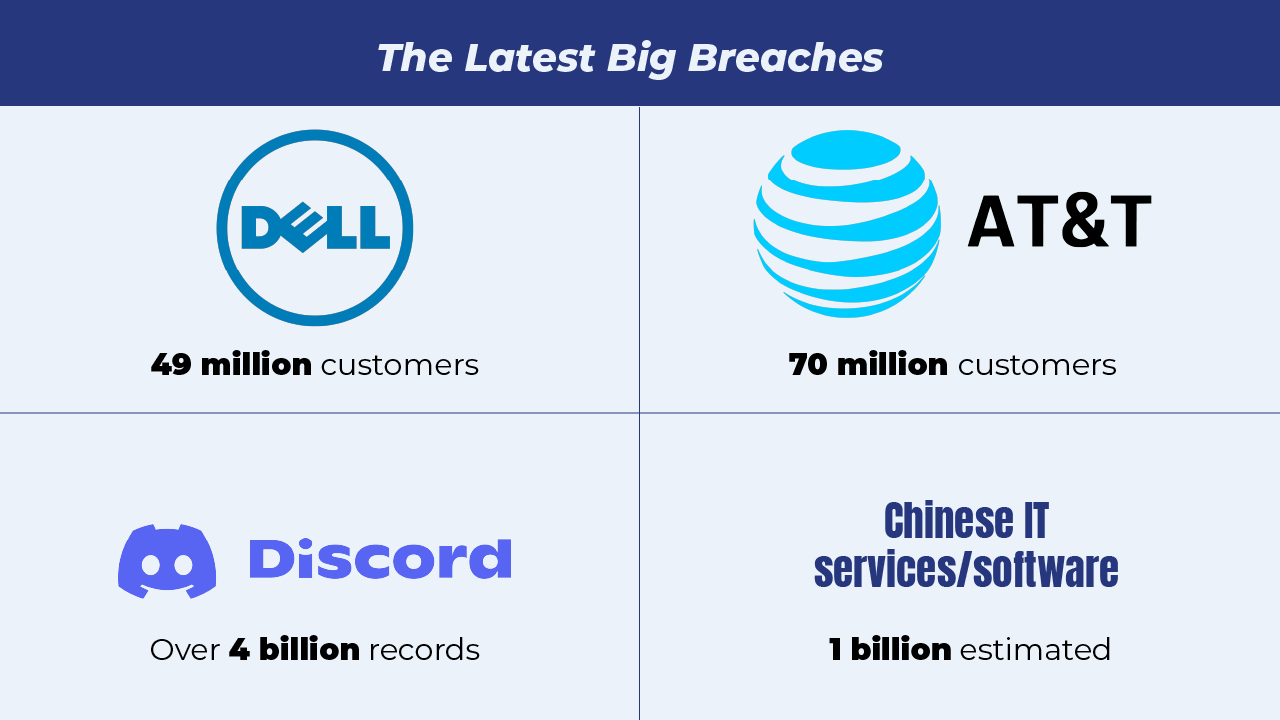
Among specific cyber threats, data breaches—both as part of ransomware double extortion and independently—continue at pace, and here are some of the largest from this period:
Data Breaches April 2024:
- Ray AI Servers: In an ongoing attack, thousands of servers in the Ray AI framework were hacked, starting in late March. It’s the responsibility of Ray’s users to authenticate, according to its maker, but security firm Oligo has observed attackers stealing AI production data, database credentials, and more, used by platforms like OpenAI, Hugging Face, and Azure. This points to the importance of properly configuring third party solutions, which can be a company’s weak point if not used diligently.
- AT&T: The telecom giant AT&T announced at the end of March they were resetting passcodes for customers (later offering credit for those affected), after an outage was followed by reports that data for as many as 73 million former and current customers had leaked. This joins a nearly continuous list of telecom breaches, such as those covered in our last roundup, and in events from 2023.
- Roku: In April, Roku revealed that hackers used credential stuffing, trying login information from prior breaches to gain access to user accounts. In a few hundred cases, these were used to make purchases, but for most of the 576,000 affected accounts, there has yet been impact. As always, it’s essential to use unique passwords for every login to prevent this kind of breach.
- Chinese IT: Up to a billion people suffered exposed data due to critical vulnerabilities in nine, cloud-based, pinyin keyboard apps from a variety of Chinese vendors. The vulnerabilities were reported to and fixed by most providers, but there have been significant vulnerabilities to surveillance for some time.
Data Breaches May 2024:
- Discord: As April ended, Discord announced it brought down Spy.pet, a website that, according to Bitdefender, scraped messages from 620 million users across more than 14,000 servers. The website sold the more than 4 billion messages to interested parties in exchange for cryptocurrency. While not a breach of Discord’s internal data, it relied on user accounts to infiltrate servers or get invite links to use for harvesting.
- Dell: In May, Dell sent emails to customers hit by their own database hack. The stolen data included name, address, hardware and order information for as many as 49 million customers, with the data being put up for sale on the dark web. It’s the kind of specific data that allows for highly personalized phishing, or social engineering attacks, such as the method used by Black Basta, where the attacker knows key information about you and your systems.
On National Security
As cybercrime is increasingly used as a weapon against rival nations, we shift to national-level security vulnerabilities and key regulatory developments:
- Threats to US Infrastructure: Wired magazine in May featured a bizarre interview with the Cyber Army of Russia Reborn, which attacked the small Texan town of Muleshoe and leaked tens of thousands of gallons of water. This came alongside numerous warnings (such as by the FBI) that the Chinese government is unrelentingly attacking US infrastructure, with attacks coming across a wide range of sectors.
- Cell Network Espionage: Again it’s telecom in the news, as a CISA official in May told the FCC that a system known as SS7—connecting cell networks by varying providers—has critical vulnerabilities. Acknowledged as already being used for internal spying, the vulnerability could also leave hundreds of millions of Americans open to espionage across the board, a warning to telcoms to do more to lock down the system.
- Government Pressures the Private Sector: In May, CISA called officially on tech companies to be “Secure by Design,” and prioritize cybersecurity in the building of their products. With the goal of bolstering a public-private cyber defense partnership (and public awareness), it remains unclear how many of the big tech players have signed on, or what impact this will have, though it shows an increasing urgency on the part of regulators.
- Cybersecurity Posture Report: In early May, the White House also released a Cybersecurity Posture report, outlining initiatives to strengthen defenses and mitigate risks. Aiming to present a strategic approach to (and prioritization of) cybersecurity, this comes as the spotty regulation on healthcare security gets a fresh look.
- World Cybercrime Index: We close our national security section with the World Cybercrime Index, released in April by Oxford University with the goal of better understanding cybercrime origination. In interviewing global cybersecurity experts actively tracking criminals, it ranks where the most dangerous cybercriminals are located, measured by impact, professionalism, and technical skill.
The results were far and away led by Russia (1), followed by Ukraine (2), China (3), the United States (4), and Nigeria (5), with the top five well ahead the rest of the world in the risk posed.
Conclusion
This is just a sampling of the latest cybersecurity events making news in April and May, but also an ongoing reminder of the necessity of being proactive in defense, both personally, and as part of organizations that are under near-constant attack.
[For help with your own cybersecurity, contact PTP to hire onsite or remote consultants.]
At Ascension, there’s been no timetable given for when the services will be back online. They’re working with federal law enforcement, and the pressure is spread across hospitals, as patients are rerouted by necessity and mortality rates increase in the fallout from this insidious crime.
Look for the next edition of our roundup around the final week of July, and until then, stay safe!
References
The Mystery of ‘Jia Tan,’ the XZ Backdoor Mastermind, Wired
#StopRansomware: Black Basta, CISA
Ongoing Social Engineering Campaign Linked to Black Basta Ransomware Operators, Rapid7
U.S. Charges Russian Man as Boss of LockBit Ransomware Group, KrebsonSecurity
Thousands of servers hacked in ongoing attack targeting Ray AI framework, Ars Technica
AT&T Resets Millions of Passcodes After Customer Records Are Leaked, New York Times
Roku says 576,000 accounts breached in cyberattack, CNN
The not-so-silent type Vulnerabilities across keyboard apps reveal keystrokes to network eavesdroppers, Munk School at the University of Toronto
Dell Confirms Database Hacked—Hacker Says 49 Million Customers Hit, Forbes
A (Strange) Interview With the Russian-Military-Linked Hackers Targeting US Water Utilities, Wired
Cyber Official Speaks Out, Reveals Mobile Network Attacks in U.S., 404 Media
The World Cybercrime Index: What is it and why is it important?, Tripwire





