We’re back for our bi-monthly cybersecurity roundup, and this time out we open on business e-mail compromises, or BEC.
As profiled in reporting by cybersecurity journalist and investigator Brian Krebs, consider the example of an unnamed transportation executive who got tricked into entering credentials on a fake Microsoft 365 login page. This resulted in the rapid mining of their emails, including several concerning company invoices.
The attackers then quickly spun up a false domain (in just hours) which looked like the legitimate business and reportedly fooled at least one customer into paying on a fictional invoice, resulting in a six-figure financial loss.
This is an example of BEC, and last year these scams were the seventh most reported crime by the FBI Internet Crime Complaint Center (IC3), but second in losses, costing companies a reported $2.8 billion in damages.
The Association of Financial Professionals found that 63% of organizations had suffered BEC last year alone.
They’re also an appropriate place to start our roundup of cybersecurity news from June and July 2025, where we cover the current data breaches (including a cache that’s been claimed as the biggest ever), the White House cybersecurity executive order, the startling success of Scattered Spider, and a look at the ongoing SharePoint crisis.
The End of Trust
As cybersecurity expert and Scamicide newsletter author Steve Weisman told Newsweek in June:
“The best way to protect yourself is to follow my rule, ‘trust me, you can’t trust anyone.’ Whenever you receive a phone call, text message or email requesting personal information, you can never be sure who is actually contacting you.”
It’s the end of trust online, or should be, something Zero Trust advocates have been promoting for decades.
It’s far easier to be fooled in a digital universe (or a digitally connected real one), and with easily accessible AI deepfakes across modalities, it gets harder to know who you’re really dealing with seemingly every single week.
To this end, if you’re receiving far more wrong-number texts this summer, you’re not alone.
Wired reported in July on the FTC’s announcement of a surge in wrong-number scams. Criminals open with innocent-seeming messages like “how’s it going?” (but can include more personal approaches like family members supposedly sending you new contact numbers), all geared to draw targets in.
These sometimes make use of AI-generated content like photos, but the best recourse is to just ignore them, block, or forward to 7726 in the US to report.
Sounds obvious, right?
But a recent study by Dojo of 2000 UK employees (including from the C-suite), found that workers and leaders alike aren’t nearly as adept at spotting scams as we think. In their study, only 3% managed to identify all the phishing emails from the genuine (57 of the 2000).
And while executives fared better at detecting legit communications in applications like Slack and email (58%, vs 36% of non-execs), leadership fared much worse at detecting AI scams, with 90% saying they believed they can.
66% of these then failed to do so.

It’s getting harder and harder to know the real from the fake, meaning the best defense for all of us may be a lack of trust in all unverified digital communications.
The Biggest Cyber Attack in History?
Researchers at Cybernews broke a leak in June of some 16 billion passwords, including for logins to some of the largest tech platforms in use.
With millions of people potentially affected, the data most likely originates from infostealers, as well as credential stuffing sets and prior breaches, and is scattered over some 30 datasets.
And while there are likely overlaps, the data is not all recycled, with researchers confirming new information was found. Wired had reported in May on one of these datasets.
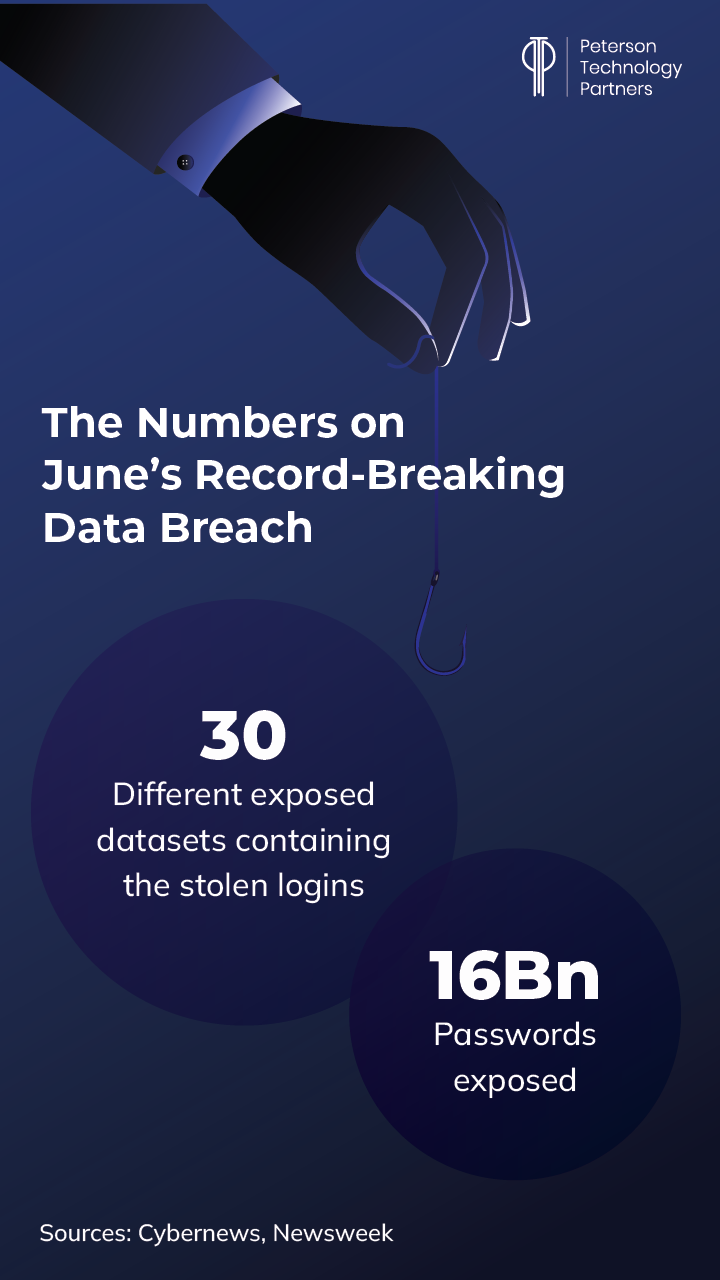
And while it may be an exaggeration to call this “the biggest breach in history,” the find points to how commonplace such enormous lists are becoming, and the incredible scale of breaches that are happening across platforms every day.
As ever, it’s critical to never reuse passwords and to enable MFA, and organizations continue to suffer from those who fail to do these simple things.
You can also check if your own login details have been leaked at sites like haveibeenpwned.
As Neringa Macijauskaitė, information security researcher at Cybernews said in Newsweek’s coverage:
“We’re facing a widespread epidemic of weak password reuse. If you reuse passwords across multiple platforms, a breach in one system can compromise the security of other accounts.”
The White House Cybersecurity Executive Order for 2025
The current administration put out its own executive order on cybersecurity in June, reversing mandates from the Biden-era and shifting the focus in some areas.
The order included eliminating the digital identities provisions, which had been encouraged and clarified in prior orders.
In AI, it focused on tracking vulnerabilities and containing issues over collaborations and pre-emptive regulations, and overall focused more on external aggressors.
The order also simplified the deadline for post-quantum cryptography (PQC).
According to the White House’s fact sheet, its goal is to improve software development, border gateway (BGP) security, post-quantum cryptography implementation, AI security and more, while preventing the potential abuse of digital identities.
On the Watch for Scattered Spider Cyberattacks
The enigmatic cybercriminal group Scattered Spider, previously connected to the extortion of US casinos and the Snowflake cloud hack, hit the spotlight again in this period, with Google’s Mandiant warning that the group was now focusing on airlines and transportation.
They’d successfully wreaked havoc in the UK retail industry in the spring, as well as the US insurance industry.
A collective that includes teens deemed extremely talented at social engineering, four arrests of suspected associates aged 17–20 were made in the UK in July.
Experts warn that the group’s decentralized nature and highly effective method of impersonating IT helpdesks is what makes them so successful.
The FBI and CISA have called on organizations to tighten authentication measures, train staff on these specific phishing techniques, and improve internal verification overall as a result of the group’s successes.
Spotlight on the SharePoint Data Breach
Earlier we teased “the biggest cyberattack ever” for a massive cache of found credentials. In truth, by severity, it may have happened a month later and still be ongoing.
Microsoft was thrust back in the cybersecurity spotlight in the period, as on-prem SharePoint systems were revealed to have been badly exploited in July.
Dubbed the ToolShell campaign, it’s believed to have already affected more than 400 organizations globally, including the US National Nuclear Security Administration.
Using zero-day flaws uncovered at the Pwn2Own contest in May 2025, the exploit enables unauthenticated remote code execution, with attackers even finding ways around the first patch that was issued July 8.
Microsoft has attributed the exploit to three Chinese-linked groups—Linen Typhoon, Violet Typhoon, and Storm-2603—with the latter also observed deploying Warlock ransomware.
Tens of thousands of on-prem SharePoint servers remain vulnerable, prompting CISA and Microsoft to issue emergency guidance, including machine key rotations and even immediate disconnection of end-of-life systems from the internet.
In short, if you run an on-prem SharePoint server and haven’t already done so, you should immediately investigate.
As Adam Meyers, Senior VP with CrowdStrike, told the Washington Post:
“Anybody who’s got a hosted SharePoint server has got a problem.”
Latest Data Breaches for June and July 2025
Major and noteworthy data breaches and updates of the period included:
- United Natural Foods was the latest target in the food industry to get hit, with the knock-on effect of shelves, fridges, and freezers at numerous American groceries (including most Whole Foods locations) being suddenly emptied. For more detail on this and other cyberattacks on the food and agriculture sector, check out our PTP Report from a two weeks ago.
- In June, the US operations of the Dutch-Belgian multinational retailer Ahold Delhaize (the fourth largest food retailer in the US and parent of store chains like Food Lion, Stop & Shop, Hannaford, and Giant Food) revealed the personal data of some 2 million customers had been leaked, following their own cyberattack last November.
Ongoing Breaches in Healthcare
- Also in 2024, Michigan’s McLaren Health Care (which had previously been hit in 2023) was breached, with investigations being run by a third-party and disclosures happening in this period. Personally identifiable information (PII) was leaked to the dark web for some 740,000 people, which included social security numbers, drivers’ licenses, and medical and health insurance details.
- Earlier this year, Episource, a healthcare analytics firm and UnitedHealth subsidiary, suffered a hack that leaked data from over 5.4 million people, according to the US Department of Health and Human Services Office for Civil Rights portal. The breach was discovered in February, and, as above, contains social security numbers, health diagnoses, and insurance records.
- Freedman Healthcare (FHC)—which runs tech services for tens of state-run public health centers, insurance companies, and nonprofits—disclosed the leak of an enormous cache (some 52GB) of company data, which per reporting by Cybernews included annual budgets, vendor contracts, insurance paperwork, inventory, client files, and more. The leak occurred over multiple years but was again disclosed in this timeframe. The company claims no protected health information (PHI) was included.
- The HIPAA Journal in June reported on a large database containing 2.7 million patient profiles (and some 8.8 million appointment records) also being leaked online. This contained names, birthdays, addresses, phone and emails, chart IDs, billing information, and more. Though the source is not identified, references in the data potential tie it to a company named Gargle that offers services for dentists.
- Around one year ago, a bad update from cybersecurity firm CrowdStrike took down millions of computers (our CEO wrote about the importance of digital resilience following the attack), and research reported by Wired in July details the specific healthcare impact—over 750 hospitals suffered disruptions, with more than 200 directly impacting patient care.
The Recruiting Cybercrime Spotlight
The recruiting industry has also suffered its share of breaches, which can expose applicants to more sophisticated fraud (using their personal data and acting as potential employers) and likewise companies, both with malware embedded in supposed applicant data and even fake applicants seeking to gain access to hack the target company.
Specific events from this period included:
- In June, resume-building site LiveCareer misconfigured a cloud storage bucket, exposing over 5 million resumes containing personal information like names, contact details, work history, and education credentials.
- Software provider TalentHook suffered a similar exposure but of even greater scale—nearly 26 million resumes were left unsecured online, constituting one of the largest leaks of this kind to date.
- Microsoft Threat Intelligence issued an alert in July 2025 (joining the FBI and others) warning of foreign-backed remote workers linked to North Korea, working to infiltrate US companies using stolen identities and even AI-generated personas. They use tactics like fake LinkedIn profiles, VPNs to obscure locations, and falsified documents to pass background checks and gain high-level access to enterprise systems. (Our CEO recently updated our prior reporting of these incidents in his last newsletter.)
- Researchers at DomainTools warned in June about a threat actor known as Skeleton Spider or FIN6 deploying ransomware acting as job seekers, making contact through platforms like LinkedIn and Indeed. The criminals use trusted cloud providers like AWS to host their infrastructure and evade detection, and work to establish a credible dialog with potential targets. What’s unique in this approach is that instead of embedding malware in submitted materials, they attempt to lure recruiters to personal/promotional websites, which can deliver a plaintext resume (if the visitor is protected), or else a Zip full of malware.
- Also in the period, the McDonald’s AI data breach stands as a unique case, as it may have exposed as much as 64 million records for applicants, but did so via an admin password “123456.” Researchers found they could easily hack into the poorly secured backend of AI tool Olivia, built for McDonalds by Paradox AI. The story points to the necessity of ensuring that all third-party partners sufficiently secure tools and services they provide.
How to Secure AI Tools? You Can Trust PTP
McDonald’s isn’t alone—there was such a large number of AI-related cybersecurity events in the period that they exceeded what we had room here to cover.
We’re planning a follow-up PTP Report focused on this topic, looking at tackling AI-first security risks and essential AI agent security issues to shore up.
But in short, it’s never been more critical to scrutinize third-party providers for their own cybersecurity protections and practices, whether they provide AI tools, consulting, or vet incoming talent.
With more than 27 years of experience delivering top tech talent and our own AI solutions, we encourage you to check out what PTP has to offer.
We incorporate the best security practices in everything we do and can also provide talent in hardest-to-find areas like cybersecurity, whether your needs are onsite or off.
Conclusion
Tom’s Hardware reported in June on the stunningly primitive state of US air traffic controller technology, which, like San Francisco subways, is still using software from the 20th century.
The FAA is seeking to modernize this system over the next four years, but it currently works on computers running Windows 95, transferring data via paper strips and floppy disks.
Ironically, this may have protected this area of critical US infrastructure from numerous cyberattacks, as well as failures like last year’s CrowdStrike outage that paralyzed so much of the world’s computing.
But being so outdated is also increasingly dangerous, given the difficulty of finding the talent and hardware necessary to maintain it.
And replacing the system, which has components which can never be fully shut down, is going to be incredibly challenging, as they face the steepest of cybersecurity challenges in whatever they ultimately implement.
It could serve as a reminder that, no matter how severe your own cybersecurity challenges may be, there’s always someone with a greater challenge out there.
Keep an eye out for our AI cybersecurity special, and until next time, you can catch up on our cybersecurity roundup coverage to date from 2025:
References
Trump Drops A Cybersecurity Bombshell With Biden-Era Policy Reversal, Forbes
Major Cyber Attacks, Ransomware Attacks and Data Breaches of June 2025, Cyber Management Alliance
Phishing statistics: Only 3% of employees could confidently spot a scam, Dojo
Inside The ToolShell Campaign, Fortinet
What to know about ToolShell, the SharePoint threat under mass exploitation and San Francisco to pay $212 million to end reliance on 5.25-inch floppy disks, Ars Technica
A Group of Young Cybercriminals Poses the ‘Most Imminent Threat’ of Cyberattacks Right Now, AI Agents Are Getting Better at Writing Code—and Hacking It as Well, How to Spot and Guard Against Wrong Number Scams, Security News This Week: 4 Arrested Over Scattered Spider Hacking Spree, and At Least 750 US Hospitals Faced Disruptions During Last Year’s CrowdStrike Outage, Study Finds, Wired
Erie Indemnity likely first ransomware attack to hit insurance sector as M&S hackers pivot, security expert warns, UnitedHealth subsidiary Episource hit with data breach, millions affected, Venkatesh Sundar, Indusface: “zero-day exploits don’t wait for your dev team to catch up”, Half of workers still can’t spot a phishing scam, even when they think they can, Freedman Healthcare says “no health data compromised” as ransomware gang dumps 52GB, and Hackers pose as job seekers: opening a resume leads to ransomware, Cybernews
Trump Cybersecurity Executive Order Targets Digital Identity, Sanctions Policies, Security Week
Major data breach at McLaren Health Care sees 743,000 patients affected – here’s what we know, Techradar
Database Containing More Than 8 Million Patient Records Exposed Online, and Episource Cyberattack Attack Affects More Than 5.4 Million Individuals, The HIPAA Journal
FAA to eliminate floppy disks used in air traffic control systems – Windows 95 also being phased out, Tom’s Hardware





