As we near the start of summer, it’s time for the next installment of our cybersecurity roundup, focused on keeping you up to speed on all the latest cybersecurity news.
As usual, there’s more to report than we have room for, but this time out we focus on AI implementation risks in business (as well as fears and use in attacks) and the continued spike in scams, then sweep through the biggest breaches, vulnerabilities, and attack trends for April and May.
Among the big stories from this period: Security researcher Jeremiah Fowler’s discovery of a mysterious, unsecured database containing more than 184 million logins from a variety of major services (including Apple, Meta, Google) and accounts linked to dozens of governments. In contacting some of those affected, he found them to be active and accurate, providing cyber criminals with dangerous access to highly significant accounts, from national security to financial data.
While it remains to be seen who is behind the list (field names appear to be in Portuguese), he suspects it was built using an infostealer.
For more on infostealers or to catch up with news you may have missed, check out our prior cybersecurity roundups from 2025:
A Cybersecurity Cautionary Tale: 23andMe
One of the major stories in May concerned a cyber attack from back in 2023, to the consumer genetic testing company 23andMe.
When attackers exploited reused passwords to access some 14,000 accounts, the company’s linking of accounts by DNA relatives opened the door to millions of additional users. Leaks including names, family members, DNA segments, and more. And as this information spread out onto the dark web, the company’s slow and problematic handling of the issue only exacerbated the problem, which spiraled into lawsuits, a massive settlement, and a severely damaged reputation.
And while there were additional business issues that led to the company’s ultimate bankruptcy, its failure to protect one of the most unchangeable aspects of a person’s identity (their genetics), coupled with their handling of it, was an undeniable contributor.
Users in May were advised to get what they needed and request removal of their data, as the company’s assets were put up for sale.
Corporate Fears about AI: Inside and Out
The 2025 Thales Data Threat Report surveyed more than 3,000 IT experts across industries and nations and found one striking similarity rise to the top: The rapid development of AI (GenAI in particular) is a huge concern for companies.
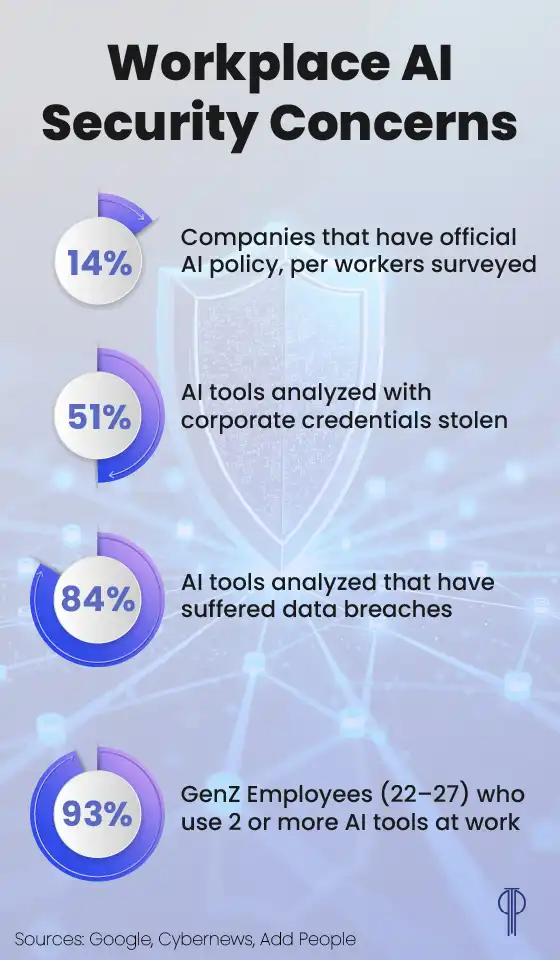
While the risks shared included integrity and trustworthiness, it was AI security that led the pack.
Among the fears:
- Lack of Sufficient Vetting Leaves Too Many Unknowns: In a rush to keep up with the rapid-changing nature of the technology, it’s difficult to fully assess the security implications of tools and providers before deployment.
- LLM Hijacking Defenses Remain Uncertain: Exposed API keys can lead to unauthorized access, for example, and prompt-injections can cause the divulging of sensitive training data.
Evaluations by outlets like the Cybernews have demonstrated this fear isn’t fully unwarranted. According to their Business Digital Index, some 90% of analyzed AI tools have been exposed to data breaches.
Misconfigurations can expose data being sent between users and tools, and a company’s attack surfaces are expanded with cloud configuration issues or outdated servers.
These risks are further compounded by the massive number of employees using AI tools for work outside of official company policy. Without a full picture of these security risks, workers may be entering sensitive company information into public systems like ChatGPT, even using personal devices.
[For more on this topic, check out the bi-weekly newsletters by PTP Founder and CEO Nick Shah, such as on the importance of establishing and communicating effective AI policies.]
As we move on into AI agents, the importance only intensifies. Carnegie Mellon professor and OpenAI board member Zico Kolter told Wired’s Will Knight that he now starts all his AI security talks focused on AI agents, because they are far less sandboxed than chatbots, and can directly impact the real world by design.
Furthermore, they string together tasks which can snowball issues, and as they collaborate with other agents (including at third-party systems), these interactions introduce variables we don’t fully understand.
[Take a look at our prior PTP Report for more on the security concerns in multi-agent systems.]
The Cyber Scams Pulse for May 2025
There is already broad use of AI for cyber attacks, but at this point the main damage may be done via scams.
With the amount lost to scams alone reaching $1 trillion a year globally (and Americans being disproportionately affected), it’s becoming difficult to trust even familiar-seeming outreach via channels like social media, text, email, and even audio and video conferencing.
In May, Google unveiled a way they’re trying to help, employing their Gemini Nano AI for anti-scam measures in the Chrome browser. Their defenses reportedly block hundreds of millions of malicious search results every day, and this addition is succeeding at flagging another 20 times more scam websites, in part by identifying interconnected networks (to other known scammers).
With scamming being big business for cybercriminals, it, like ransomware, is inspiring whole systems devoted to the teaching and executing effective techniques. Wired in May reported on Format Boy, a scam influencer with popular social media channels who acts as an advisor to the West African scam ring known as the Yahoo Boys.
Among their fraudulent activities: fake CNN broadcasts with AI-generated hosts, face-swapping video calls, and extensive social engineering campaigns that can take weeks or even months to execute and aim at robbing people of savings.
The Chinese-speaking group known as the Smishing Triad sends millions of fraudulent texts mimicking legitimate companies, all aimed to lead targets to fake websites that can steal personal and financial information.
We’ve reported previously on a method of North Korean cyber fraud, where operatives infiltrate the global IT workforce, sometimes even doing legitimate, quality work (but under a false identity and from an illegal location, with the added risk of hacking company systems if they are exposed).
This initiative again made news this period as the scale of these scams was revealed to be larger than initially known.
Noteworthy Data Breaches and Hacks in the Period
Increasingly, state-sponsored acts of cyber espionage also have links to criminal hacking, and one large example came to light in May, as the US Department of Justice charged Russian individuals linked to the DanaBot malware operation.
Since 2018, this malware has infected millions of systems worldwide, and allegedly also exists as a “for pay” version. CrowdStrike found DanaBot lurking in the JavaScript tool NPM in 2021 as a form of supply chain attack that had millions of weekly downloads.
Other threats related to foreign powers that are in the news (or back again) include:

Misconfiguration fears can keep CISOs up at night, and for good reason. In this period we see several examples, from the database file of high-profile logins we lead with to AI tool vulnerabilities to our latest incidents, which found 200 billion files exposed by misconfigured cloud storage buckets.
Spanning seven major cloud providers, the leaked data included credentials and source code as well as documents and internal backups, with millions of the files believed to also contain sensitive information.
Security firm Cyble, who discovered the leak, warns this is a common form of data leakage that can stem from the complex relationships between systems that involve sharing documents or resources.
The Cybersecurity and Infrastructure Security Agency (CISA) issued a security alert in April that advised enterprise customers of Oracle to reset passwords and review credentials across servers ASAP. This followed confirmation by Oracle of a breach of legacy servers that leaked credentials including usernames, email addresses, passwords, authentication tokens, and encryption keys.
Data Breaches from May 2025 of Questionable Scale and Legitimacy
Cybernews researchers in May found a massive trove of Facebook data (from an alleged 1.2 billion users) on the dark web. It is supposedly all new, obtained by abusing the Meta API, and contains user IDs, names, email addresses, usernames, phone numbers, locations, birthday data, and more.
The researchers found their surveyed samples to be accurate, though they remained skeptical of the total number. Meta did not deny the breach, but instead suggested the data was old.
Valve, the company behind Steam, squashed claims in May that data from 89 million accounts were leaked. The dark web data store made news when it was put up for sale, but the company said the “breach” really only contained logs of outdated text messages with two-factor authentication codes and posed no risk to users.
Employment Service Leaks
Also from misconfigured cloud storage, millions of job seekers had their personal information potentially exposed, including:
- HireClick: The US recruitment platform for small-to-medium sized businesses may have exposed some 5.7 million files due to Amazon AWS storage bucket misconfigurations.
- beWanted: The popular European jobs platform was found to have exposed records for as many as a million individuals through an open Google Cloud Storage bucket, and at the time of this writing it was still open.
DDoS Is Having a Big Moment
There also were some of the largest Distributed Denial of Service (DDoS) attacks ever seen during this period. According to Cloudflare, Q1 of 2025 witnessed a 358% increase over the prior year, and saw a particularly intense (if brief) campaign launched in April.
One of these targeted cybersecurity blog KrebsOnSecurity, hitting it with an attack that peaked at 6.3 terabits of data per second.
At 10 times the size of a DDoS attack that took the blog offline for four days back in 2016 (and made the host wary of keeping him), it was the largest ever handled by Google’s Project Shield and second only to an attack in the same period recorded by Cloudflare.
Making use of a massive IoT botnet, the KrebsOnSecurity attack was very brief (just 45 seconds), and is believed to have been a test to show off the botnet’s potential for buyers.
Popular Brands Under Attack
- Coca-Cola suffered a breach of data for nearly a thousand employees in this period.
- Fashion brand Dior suffered a breach of contact information, purchasing data, and customer preferences in Asia.
- Adidas customer data was accessed through a third-party service provider but is believed to have only contained contact information related to customer service help (did not include financials or passwords).
- British retailer Marks & Spencer suffered costly outages due to ransomware, attributed to Scattered Spider. The breach began in February, when the attacker stole a Windows file containing password hashes which were then cracked, allowing lateral movement. This may also have originated via a third-party service provider.
Assaults on Infrastructure
- North America’s largest steel producer Nucor had to temporarily cease production in May after a cyberattack, taking systems offline to enact their response plan. More details are still forthcoming.
- The Novia Scotia Power utility in Canada confirmed they were also victims of a ransomware attack which began in May. While customer data was leaked, electricity generation remained unaffected, and they did not pay the ransom.
- Overall, the Cybernews found that 50% of the world’s top oil and gas providers experienced a data breach within this period alone (a 30-day period prior to May 20, 2025). Their research found that basic security failures (like unpatched software, poor email security, and yes, misconfigurations) plagued some 90% of companies surveyed.
Crypto Crime Corner
We spotlight cryptocurrency security news this period as there were some particularly noteworthy attacks, including:
- The FBI reporting that investment fraud involving cybercurrencies accounted for $6.5 billion in losses in 2024.
- TraderTraitor (see above) executed the largest crypto heist to date, with $1.5 billion stolen.
- Coinbase, the largest US crypto exchange, divulged a data breach in May, after refusing to pay a reported $20 million ransom demand. The leaked data included names, personal data, government ID numbers, account information, partial social security numbers and partial bank accounts.
Secure Your AI and Protect Yourself from AI-Powered Cyberattacks with PTP
When facing this ongoing pressure from attackers, there is no substitute for expertise, and vacancies in the hard-to-fill positions like cybersecurity and AI/ML only make it harder for organizations to protect themselves.
Whether it’s cloud configurations, software testing, SOC, monitoring, or safe AI implementations, PTP is ready to help.
With more than 27 years of experience in filling the hardest-to-get positions in tech, consider us when you are in need.
Conclusion
That ends our coverage of the major cyberattacks from April-May 2025.
Sadly, there continues to be more to cover than we have room for here, so stay tuned to The PTP Report for weekly reports that can go deeper into breaking cybersecurity, data science, and AI news!
References
23andMe Bankruptcy Filing—What 15 Million Users Should Do Now, Forbes
Businesses are overwhelmingly concerned about the security threats of AI, and Hacker claims to have grabbed 1.2 billion Facebook user records – here’s what we know, and Over 1.1 million user files leaked following huge data breach at top jobseeker platform, TechRadar
Are your AI tools secure? New analysis reveals gaps among market leaders, Analysis of AI tools: 84% breached, 51% facing credential theft, Massive data leak: 200 billion files exposed in cloud buckets, and Over 50% of the top oil and gas companies suffered data breaches in the past 30 days, Cybernews
Mysterious Database of 184 Million Records Exposes Vast Array of Login Credentials, How to Win Followers and Scamfluence People, and Feds Charge 16 Russians Allegedly Tied to Botnets Used in Ransomware, Cyberattacks, and Spying, Wired
False alarm: Valve confirms that nobody hacked into over 89M Steam accounts and that your passwords are safe, PC Gamer
Misconfigured HireClick storage bucket exposes over 5.7M files, SC Media
Targeted by 20.5 million DDoS attacks, up 358% year-over-year: Cloudflare’s 2025 Q1 DDoS Threat Report, The Cloudflare Blog
KrebsOnSecurity Hit With Near-Record 6.3 Tbps DDoS, KrebsOnSecurity
Marks & Spencer breach linked to Scattered Spider ransomware attack, Bleeping Computer
Production at Steelmaker Nucor Disrupted by Cyberattack, Security Week
CISA issues Security Alert for Customers Affected by Oracle Data Breach, The HIPAA Journal
Coinbase Reveals Over 69,000 People Had Their Data Exposed in a Breach. Take These Steps Now, CNET





